Data Breach Aftermath: Long-Term Impact & Prevention Measures
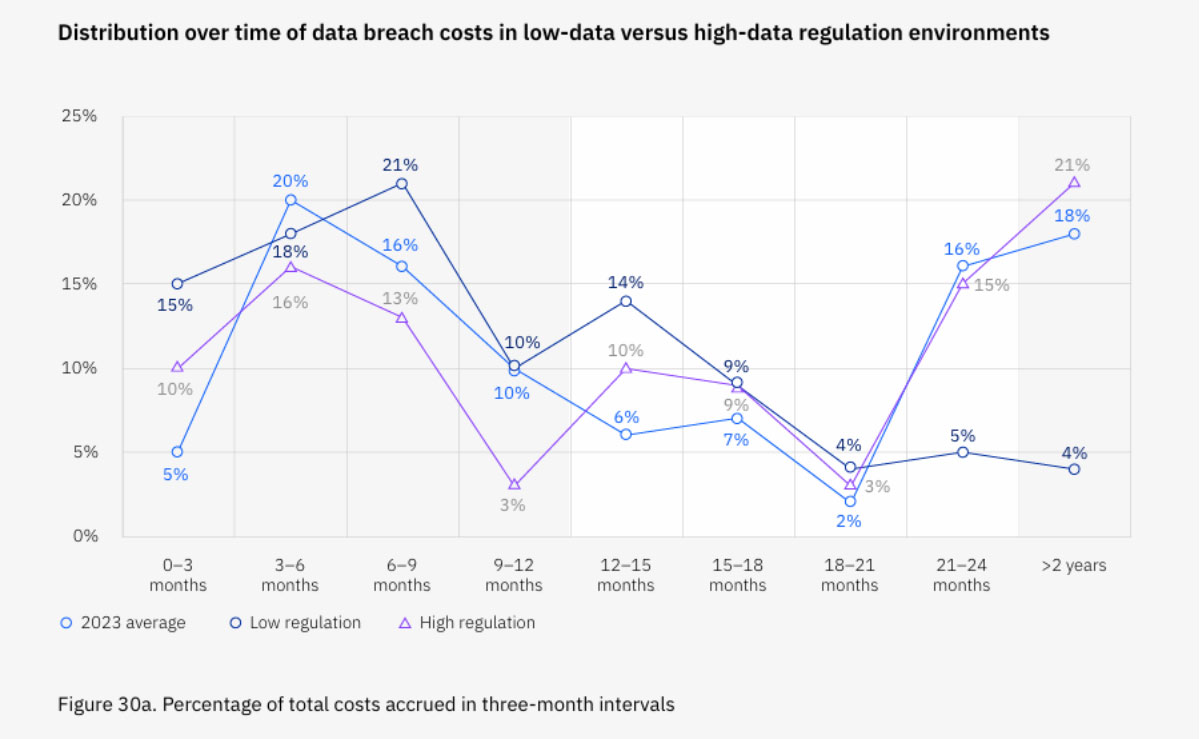
In the era of digitalization, data stands as the life force of your business, driving operations, strategic choices, and customer engagements. However, within this data-focused realm lies a significant concern – the looming threat of data breaches. Data breaches have lasting repercussions for businesses, with only 51% of costs occurring in the first year post-incident. The remaining 49% unfold beyond year two. We will explore the lasting effects of a data breach and delve into a real-life case study. Discover how a single breach can have lasting repercussions, affecting a company’s reputation, financial health, and compliance status.
Data Breach: The Hidden Expenses
Exploring the First American Title Insurance Co. Case
The 2019 cybersecurity breach at First American is a glaring example highlighting the extensive repercussions of a data breach. The case involved a $1 million penalty imposed by the New York Department of Financial Services (NYDFS), with reports of the fine surfacing in the autumn of 2023. The fine resulted from the company’s failure to protect sensitive consumer data adequately. The breach exposed more than 880 million documents containing personal and financial information, demonstrating a significant breach of data protection protocols.
This is just one example of how expenses can linger long after the initial breach. Below are additional ways in which security incidents can continue to impact businesses over an extended period.
The Aftermath of a Data Breach
Financial Consequences
A data breach carries a heavy financial burden. Immediate expenses encompass:
Detecting the breach
Containing it
Notifying customers
In addition, businesses encounter lasting costs such as legal disputes, regulatory fines, and compensations. Regulatory penalties represent just one aspect of the financial fallout. Other aspects include potential legal challenges from affected individuals and class-action lawsuits that further strain finances.
Reputation Damage
One of the most enduring consequences for a business is the impact on its reputation. When customers no longer trust a company to safeguard their sensitive information, it can lead to reduced customer retention, difficulty acquiring new customers, and lasting harm to the brand’s image.
Rebuilding a damaged reputation is time-consuming and requires deliberate efforts, including public relations campaigns and enhanced security measures. These actions demonstrate a renewed commitment to data protection and help reassure stakeholders.
Increased Regulatory Oversight
As regulatory bodies tighten their grip, businesses face a growing responsibility to protect consumer data. Any data breach attracts regulatory attention, potentially resulting in fines and continuous compliance demands.
Regulatory entities adopt a strict approach to data protection. Businesses that neglect cybersecurity practices face severe repercussions, including financial penalties, increased oversight, and mandatory security upgrades.
Operational Disruption
Following a data breach, normal business operations are thrown into disarray. Remedial actions and heightened security measures become imperative for companies, and these endeavors can draw resources away from core business functions.
The repercussions are felt company-wide, impacting productivity and efficiency. The cascading effects of operational disruption may persist for years, stunting growth and impeding the organization’s agility in response to market shifts.
Customer Churn and Acquisition: Overcoming Key Challenges
A data breach frequently results in customer turnover as individuals lose trust in the company’s data security measures. Attracting new customers becomes difficult, with potential clients reluctant to engage with a brand that has experienced a breach. The enduring impact on customer acquisition can impede the company’s growth and market competitiveness.
A Cautionary Tale for Businesses Everywhere
The aftermath of a data breach goes well beyond the initial incident, affecting a company’s financial well-being and reputation long term, in addition to its regulatory compliance.
Given the escalating frequency and complexity of cyber threats, taking proactive cybersecurity measures is no longer just a recommendation but a strategic necessity to ensure the enduring prosperity of businesses.
The genuine cost of a data breach isn’t always immediately apparent, encompassing a multifaceted interplay of factors like:
Financial penalties
Reputation harm
Regulatory repercussions
Operational disturbances
These effects can endure for years, underscoring the significance of drawing insights from practical scenarios. Emphasizing the implementation of strong cybersecurity practices aids in businesses’ efforts to reduce the threats linked to data breaches. This, in turn, safeguards both their immediate concerns and long-term sustainability.
Protect Your Business from Cyber Threats with a Comprehensive Cybersecurity Assessment
Cyber attackers have various methods to breach networks, targeting endpoints and cloud services. It’s crucial to ensure robust security measures. Looking for guidance? Book a cybersecurity assessment now with Solve IT Solutions. This proactive approach helps you identify and mitigate risks, preventing data breaches and their repercussions.
Contact us today to arrange a consultation and fortify your defenses against cyber threats.
About Solve IT Solutions
Solve IT Solutions, LLC offers relationship-based technology solutions to more than 200 small and midsize businesses in Eastern Pennsylvania. From the Company’s inception in 2000, the principal Troy Kantner saw a need for affordable IT solutions with an understandable approach. Today, Solve IT Solutions has grown to provide a full line of services that meet those needs. Offerings by Solve IT Solutions include managed and co-managed IT services, business continuity and disaster recovery services, network solutions, data center offerings, network security and assessment, data migration, cyber security, and more. Solve IT Solutions, LLC has proudly achieved recognition as a winner of the prestigious Channel Futures MSP 501 in both 2021 and 2022. Additionally, we are honored to have consistently appeared on The Greater Reading Chamber Alliance Business Excellence Award List for the past nine years in a row. We are grateful for these acknowledgments, which affirm our commitment to excellence and our dedication to delivering exceptional IT solutions. Solve IT Solutions, LLC is located at 501 N. Park Road, Wyomissing, Pennsylvania.